"ShellForge is a python program that builds shellcodes from C. It is inspired from Stealth's Hellkit. Some wrapper functions arround system calls are defined in header files. The C program uses them instead of libc calls. ShellForge uses gcc to convert it into assembler. It then modifies it a bit, compiles it, extract code from the object, may encode it and add a loader at the begining." read more...
"ShellForge is a python program that builds shellcodes from C. It is inspired from Stealth's Hellkit. Some wrapper functions arround system calls are defined in header files. The C program uses them instead of libc calls. ShellForge uses gcc to convert it into assembler. It then modifies it a bit, compiles it, extract code from the object, may encode it and add a loader at the begining." read more...miércoles, 22 de abril de 2020
ShellForge
 "ShellForge is a python program that builds shellcodes from C. It is inspired from Stealth's Hellkit. Some wrapper functions arround system calls are defined in header files. The C program uses them instead of libc calls. ShellForge uses gcc to convert it into assembler. It then modifies it a bit, compiles it, extract code from the object, may encode it and add a loader at the begining." read more...
"ShellForge is a python program that builds shellcodes from C. It is inspired from Stealth's Hellkit. Some wrapper functions arround system calls are defined in header files. The C program uses them instead of libc calls. ShellForge uses gcc to convert it into assembler. It then modifies it a bit, compiles it, extract code from the object, may encode it and add a loader at the begining." read more...KillShot: A PenTesting Framework, Information Gathering Tool And Website Vulnerabilities Scanner
Why should i use KillShot?
You can use this tool to Spider your website and get important information and gather information automaticaly using
whatweb-host-traceroute-dig-fierce-wafw00f or to Identify the cms and to find the vulnerability in your website using Cms Exploit Scanner && WebApp Vul Scanner Also You can use killshot to Scan automaticly multiple type of scan with nmap and unicorn . And With this tool You can Generate PHP Simple Backdoors upload it manual and connect to the target using killshotThis Tool Bearing A simple Ruby Fuzzer Tested on
VULSERV.exe and Linux Log clear script To change the content of login paths Spider can help you to find parametre of the site and scan XSS and SQL.Use Shodan By
targ optionCreateAccount Here Register and get Your aip Shodan AIP And Add your shodan AIP to
aip.txt < only your aip should be show in the aip.txt > Use targ To search about Vulnrable Targets in shodan databases.Use
targ To scan Ip of servers fast with Shodan.KillShot's Installation
For Linux users, open your Terminal and enter these commands: If you're a Windows user, follow these steps:
- First, you must download and run Ruby-lang setup file from RubyInstaller.org, choose Add Ruby executables to your PATH and Use UTF-8 as default external encoding.
- Then, download and install
curl(32-bit or 64-bit) from Curl.haxx.se/windows. After that, go to Nmap.org/download.html to download and install the lastest Nmap version. - Download killshot-master.zip and unzip it.
- Open CMD or PowerShell window at the KillShot folder you've just unzipped and enter these commands:
ruby setup.rb
ruby killshot.rb
KillShot usage examples
Easy and fast use of KillShot:
Use KillShot to detect and scan CMS vulnerabilities (Joomla and WordPress) and scan for XSS and SQL:
References: Vulnrabilities are taken from
Use KillShot to detect and scan CMS vulnerabilities (Joomla and WordPress) and scan for XSS and SQL:
References: Vulnrabilities are taken from
More articles
How To Start | How To Become An Ethical Hacker
Are you tired of reading endless news stories about ethical hacking and not really knowing what that means? Let's change that!
This Post is for the people that:
- Have No Experience With Cybersecurity (Ethical Hacking)
- Have Limited Experience.
- Those That Just Can't Get A Break
OK, let's dive into the post and suggest some ways that you can get ahead in Cybersecurity.
I receive many messages on how to become a hacker. "I'm a beginner in hacking, how should I start?" or "I want to be able to hack my friend's Facebook account" are some of the more frequent queries. Hacking is a skill. And you must remember that if you want to learn hacking solely for the fun of hacking into your friend's Facebook account or email, things will not work out for you. You should decide to learn hacking because of your fascination for technology and your desire to be an expert in computer systems. Its time to change the color of your hat 😀
I've had my good share of Hats. Black, white or sometimes a blackish shade of grey. The darker it gets, the more fun you have.
If you have no experience don't worry. We ALL had to start somewhere, and we ALL needed help to get where we are today. No one is an island and no one is born with all the necessary skills. Period.OK, so you have zero experience and limited skills…my advice in this instance is that you teach yourself some absolute fundamentals.
Let's get this party started.
- What is hacking?
Hacking is identifying weakness and vulnerabilities of some system and gaining access with it.
Hacker gets unauthorized access by targeting system while ethical hacker have an official permission in a lawful and legitimate manner to assess the security posture of a target system(s)There's some types of hackers, a bit of "terminology".
White hat — ethical hacker.
Black hat — classical hacker, get unauthorized access.
Grey hat — person who gets unauthorized access but reveals the weaknesses to the company.
Script kiddie — person with no technical skills just used pre-made tools.
Hacktivist — person who hacks for some idea and leaves some messages. For example strike against copyright.
- Skills required to become ethical hacker.
- Curosity anf exploration
- Operating System
- Fundamentals of Networking
Related posts
lunes, 20 de abril de 2020
OWASP-ZSC: A Shellcode/Obfuscate Customized Code Generating Tool
About OWASP-ZSC
OWASP ZSC is open source software written in python which lets you generate customized shellcodes and convert scripts to an obfuscated script. This software can be run on Windows/Linux/OSX with Python 2 or 3.
What is shellcode?: Shellcode is a small codes in Assembly language which could be used as the payload in software exploitation. Other usages are in malwares, bypassing antiviruses, obfuscated codes...
You can read more about OWASP-ZSC in these link:
- OWASP ZSC Tool Project - OWASP
- Document: OWASP ZSC · GitBook (Legacy)
- Home page: OWASP ZSC | OWASP ZCR Shellcoder
- Features: OWASP ZSC | OWASP ZCR Shellocder Available Features
- Archive: ZCR-Shellcoder-Archive
- Mailing List: Google Groups
- API: api.z3r0d4y.com
Another good reason for obfuscating files or generating shellcode with OWASP-ZSC is that it can be used during your pen-testing. Malicious hackers use these techniques to bypass anti-virus and load malicious files in systems they have hacked using customized shellcode generators. Anti-virus work with signatures in order to identify harmful files. When using very well known encoders such as
msfvenom, files generated by this program might be already flagged by Anti-virus programs.Our purpose is not to provide a way to bypass anti-virus with malicious intentions, instead, we want to provide pen-testers a way to challenge the security provided by Anti-virus programs and Intrusion Detection systems during a pen test.In this way, they can verify the security just as a black-hat will do.
According to other shellcode generators same as Metasploit tools and etc, OWASP-ZSC using new encodes and methods which antiviruses won't detect. OWASP-ZSC encoders are able to generate shell codes with random encodes and that allows you to generate thousands of new dynamic shellcodes with the same job in just a second, that means, you will not get the same code if you use random encodes with same commands, And that make OWASP-ZSC one of the best! During the Google Summer of Code we are working on to generate Windows Shellcode and new obfuscation methods. We are working on the next version that will allow you to generate OSX.
OWASP-ZSC Installation:
You must install Metasploit and Python 2 or 3 first:
- For Debian-based distro users:
sudo apt install python2 python3 metasploit-framework - For Arch Linux based distro users:
sudo pacman -S python2 python3 metasploit - For Windows users: Download Python and Metasploit here.
sudo):DISCLAIMER: THIS SOFTWARE WAS CREATED TO CHALLENGE ANTIVIRUS TECHNOLOGY, RESEARCH NEW ENCRYPTION METHODS, AND PROTECT SENSITIVE OPEN SOURCE FILES WHICH INCLUDE IMPORTANT DATA. CONTRIBUTORS AND OWASP FOUNDATION WILL NOT BE RESPONSIBLE FOR ANY ILLEGAL USAGE.
An example of OWASP-ZSC
Related news
- Hacking Tools For Games
- Hacking Tools Usb
- Hack Tools Pc
- Hacker Tools Apk
- Hacking Tools 2019
- Hacking Tools For Windows 7
- Hacker Tools 2019
- Pentest Tools Free
- Nsa Hacker Tools
- Hack Tools Download
- Hacking Tools For Windows 7
- Hacker Tool Kit
- Hackrf Tools
- Growth Hacker Tools
- Pentest Tools Open Source
- Hacking Tools 2020
- Hacker
- Hacker Tools Github
- Nsa Hack Tools
- Hacker Tools Online
How To Recover Files That Are Deleted From Recycle Bin

How To Recover Files That Are Deleted From Recycle Bin
How To Recover Files That Are Deleted From Recycle Bin
Well, Windows users have a bad habit of removing files from recycle bin. Deleting useless files from Recycle Bin helps a user to save some storage space which can improve the speed of a computer. However, Windows users do that more frequently and later regret. Actually, Recycle Bin is a place from where we can get back our deleted files and folders.
Sometimes, we accidentally delete our important files and folders and due to some reason we lose them from Recycle bin too! At that time, we search for recovery methods. Well, there are many methods available over the web which can help you to recover deleted files from computer, but, when it comes to reliability, nothing can beat EaseUS.
What Is EaseUS Data Recovery Wizard?
EaseUS is one of the leading software providers which is known for its data recovery programme. EaseUS offers some free data recovery software that can help you to recover deleted, formatted or lost data from PC, laptop or removable device easily and quickly.
One of the best thing about EaseUS is that it provides tools for recycle bin recovery which can help you to get back files that you have deleted from the Recycle bin itself. EaseUS Data Recovery Wizard free can easily recover lost files, pictures, documents, videos and more from deleting, formatting, partition loss, OS crash, virus attack and other data loss cases.
How To Recover Deleted Files?
If you are struggling to get back your lost data files, then here is an easy data recovery method which will help you to get back deleted files on your computer. Below, we are going to share a mini guide on how to use EaseUS Recycle Bin Recovery to get back your deleted data.
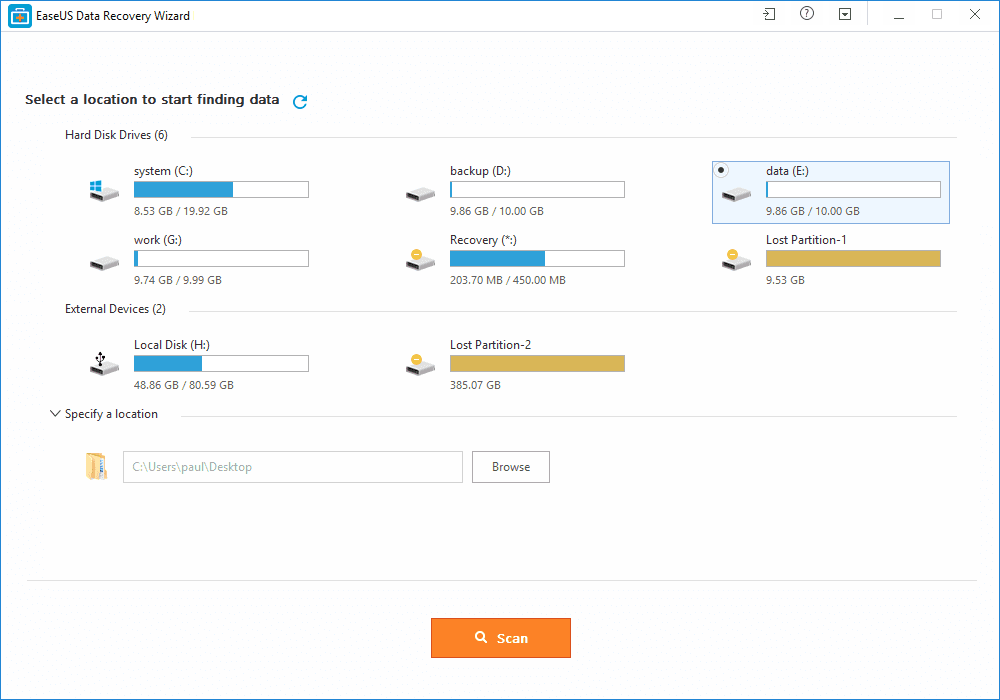
Step 1. First of all, you need to download and install EaseUS Data Recovery Wizard on your Windows computer and then launch it normally. You need to select the location where you want to scan and then click on 'Scan'
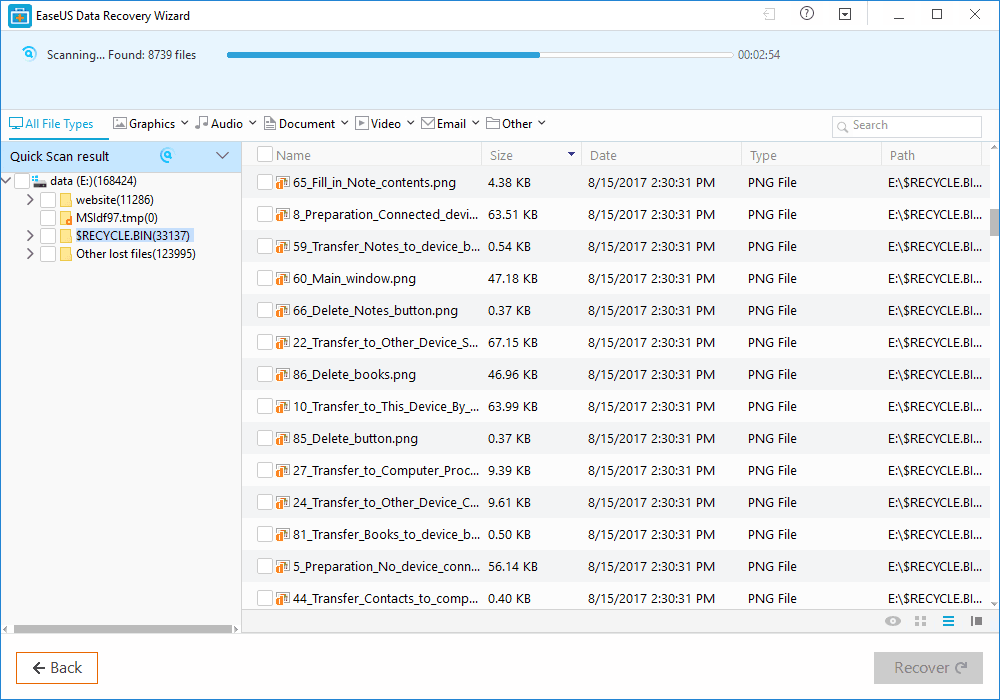
Step 2. Now, wait for few minutes until the tool finishes scanning your drive. The tool search for files that got deleted or cleaned from the Recycle Bin.
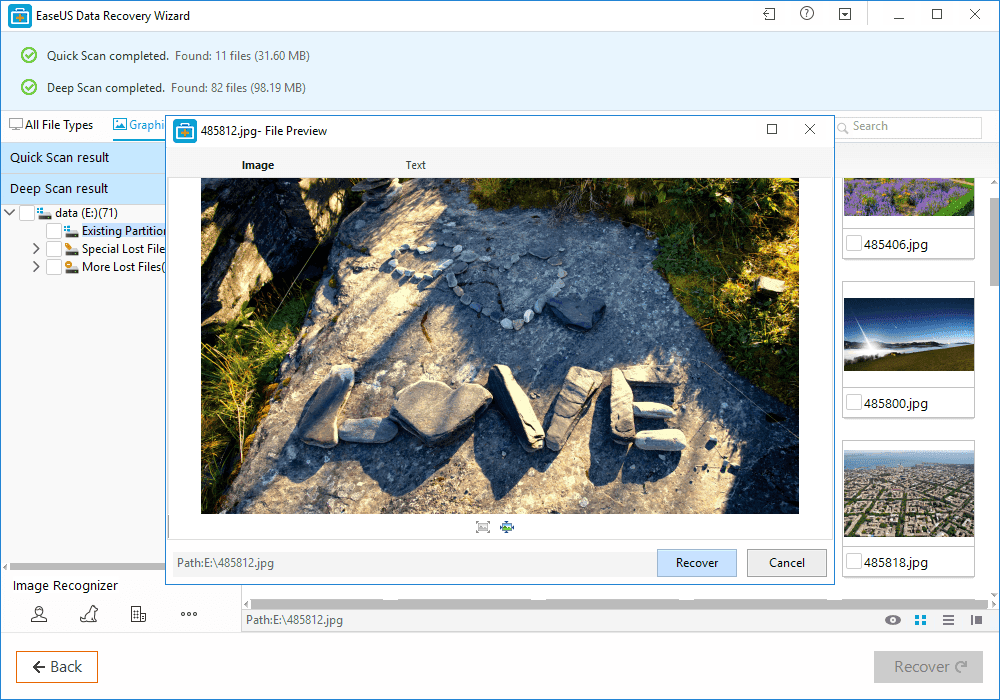
Step 3. Now it will show you files that you can recover. Here you need to click on the file which you want to recover and click on 'Recover'
That's it, you are done! This is how you can use EaseUS data recovery to get back your deleted files on your computer.
Benefits of EaseUS Data Recovery
Well, the data recovery tool provided by EaseUS comes with many benefits. It can not only recover accidentally deleted files, but it can also recover data in case of Virus Attacks, Hard Disk Damage, OS Crash etc.
You can also use this awesome data recovery wizard to recover deleted files from External Disk, USB Drive, Camcorder, Mobile Devices, Zip Drive, iPod, Music Player and more.
Overall, this is one of the best data recovery tools you can have on your Windows computer. EaseUS Data Recovery also has a free version with restricted features. Overall, this is a stress-free solution to get back your deleted files
- Hack Tools Online
- Hacking Tools For Windows
- Hackrf Tools
- How To Make Hacking Tools
- Pentest Tools Alternative
- Hacking Tools Download
- Hacking Tools For Pc
- Best Hacking Tools 2019
- Pentest Tools Alternative
- Hacker Security Tools
- Hacking Tools For Games
- Hacker Tools For Ios
- Hack Tools For Mac
- Pentest Tools Website
- Wifi Hacker Tools For Windows
- Free Pentest Tools For Windows
- Tools Used For Hacking
- Hacker Hardware Tools
- Pentest Tools Download
- Hacker Tools Apk Download
- Pentest Reporting Tools
- Hack Tools For Games
- Hacking Tools Pc
- Pentest Tools For Ubuntu
- Hack Tools Github
- Hack Tools Pc
- Hacking Tools
Evil Limiter: Taking Control Of Your Network Bandwidth
Ever wanted to block someone from the network or limit their bandwidth without having the network admin privileges? Well Evil Limiter has got you covered then.
An amazing tool to help you control your network without having access to the admin panel.
Today I'm gonna show you how to use this interesting tool to take control of your network.
Requirements:
1. A PC or Laptop with Linux OS.2. A Network Adapter.
3. Access to the Network you want to control.
4. sudo or root access on your Linux OS.
First of all we will download the tool from its github repository:
https://github.com/bitbrute/evillimiter
You can download and extract the zip file from the link above or you can clone evillimiter repository using git like this:
git clone https://github.com/bitbrute/evillimiter
Now lets install the downloaded tool on our machine
Step 1: Move inside the downloaded github repository
cd evillimiter
Step 2: To install type
sudo python3 setup.py install
wait for the installation to finish (May take some time)
Step 3: To run type
sudo evilimiter
Voila! That's it, you got it up and running on your machine
Now how do you control your network with it, its very easy.
It should detect your network automatically but yeah you can set it up manually as well using the command line argument -i.
After you have selected the right interface to control, you need to scan your network for live hosts. To perform the scan type
scan
you can pass an optional flag to the scan command which is range which will help you to specify the range of ip addresses you want to scan like this
scan --range 192.168.1.1-192.168.1.100
The above command will scan a total of 100 hosts from 192.168.1.1 to 192.168.1.100
Now after you have scanned your network next thing is to list the hosts that have been discovered during the scan for that you type the hosts command like this
hosts
Now you know the hosts on your network and now you should know which host you wanna block or limit based on the mac address of the host. Remember the host id of the host that you want to block or limit bandwidth of and lets do the magic.
to block a host from using the internet we simply specify the block command followed by the host id of the host that we want to block like this
block 1
if instead of blocking the host we just want to limit his internet bandwidth we can do just that by using the limit command followed by the host id and then the bandwidth that we want to allocate to that particular host like this
limit 1 100kbits
Wohooo! yeah its that easy and yes you can do all this without having the network admin role.
Now if you want to show mercy on that poor guy (blocked host), you can set him free by using the free command followed by the host id like this:
free 1
Well isn't administrating your network bandwidth so easy now.
Hope you enjoyed this tutorial.:)
More info
- Hack Tools For Windows
- Pentest Automation Tools
- Pentest Tools Subdomain
- What Are Hacking Tools
- Black Hat Hacker Tools
- Pentest Box Tools Download
- Pentest Tools Free
- Hacking Tools For Windows Free Download
- Hacking Tools For Windows
- Pentest Tools For Ubuntu
- Pentest Tools Alternative
- Pentest Tools Bluekeep
- Usb Pentest Tools
- How To Make Hacking Tools
- Hacking Tools Mac
- Hack Tools For Pc
- Pentest Tools For Android
- Hacking Tools For Kali Linux
- Pentest Tools Url Fuzzer
- Pentest Box Tools Download
- Hacking Tools Mac
- Hacker Tools For Mac
- Hack Tools For Ubuntu
- Hacking App
- Hacking Tools 2019
domingo, 19 de abril de 2020
DOWNLOAD COWPATTY WIFI PASSOWORD CRACKING TOOL
COWPATTY WIFI PASSWORD CRACKING TOOL
CoWPAtty is a wifi password cracking tool. Implementation of a dictionary attack against WPA/WPA2 networks using PSK-based authentication (e.g. WPA-Personal). Many enterprise networks deploy PSK-based authentication mechanisms for WPA/WPA2 since it is much easier than establishing the necessary RADIUS, supplicant and certificate authority architecture needed for WPA-Enterprise authentication. Cowpatty can implement an accelerated attack if a precomputed PMK file is available for the SSID that is being assessed. Download coWPAtty wifi password cracking tool.
It's a pre-built tool for Kali Linux which you can find in the /usr/local/bin directory. It's also available for the windows but it doesn't work as fine as it does in the Kali.
DOWNLOAD COWPATTY WIFI PASSWORD CRACKING TOOL
For windows, you can download it from here. As it becomes pre-built in Kali, you do not need to download it. You just have to follow the path /usr/local/bin directory to find it in your Kali Linux OS.
- Hacker Tools List
- Physical Pentest Tools
- Hacker Search Tools
- Hacker Tools
- Hacker Tools Mac
- Hacking Tools Pc
- Hacking Tools Kit
- Hacking Tools Github
- Hacker Techniques Tools And Incident Handling
- Hackers Toolbox
- Pentest Tools Android
- Black Hat Hacker Tools
- Github Hacking Tools
- Hak5 Tools
- Hackrf Tools
- Hack Tool Apk No Root
- Hackrf Tools
- Hack Tools For Games
Suscribirse a:
Entradas (Atom)